
What are the non-ideal effects in the current mode circuit?
In a current mode circuit, there can be several non-ideal effects that can impact its performance. Here are some common non-ideal effects:
- Non-Zero Output Impedance: Ideally, the output impedance of a current source is zero, but in practice, it can have a finite value. This can cause a voltage drop across the output impedance when driving a load, leading to inaccuracies in the current delivery.
- Output Voltage Variation: In an ideal current mode circuit, the output voltage remains constant regardless of the load impedance. However, non-idealities such as output impedance, power supply variations, or temperature changes can cause the output voltage to vary, affecting the accuracy and stability of the circuit.
- Current Source Accuracy: The accuracy of a current source is determined by its ability to deliver a constant current regardless of external factors. Non-ideal effects such as temperature changes, component tolerances, and process variations can lead to deviations from the desired current value, reducing the accuracy of the circuit.
- Sensitivity to Load Impedance: Current mode circuits may exhibit sensitivity to variations in the load impedance. Changes in the load impedance can affect the output voltage and current, introducing errors and impairing the circuit’s performance.
- Noise: Current mode circuits can be susceptible to various sources of noise, including thermal noise, shot noise, and flicker noise. These noise sources can introduce random variations in the current signal, reducing the signal-to-noise ratio and degrading the overall performance of the circuit.
- Bandwidth Limitations: Current mode circuits may have limited bandwidth due to the parasitic capacitance and inductance associated with the circuit components. These parasitic elements can introduce high-frequency roll-off and phase shifts, limiting the circuit’s ability to accurately respond to fast-changing input signals.
- Power Supply Sensitivity: Changes in the power supply voltage can impact the performance of current mode circuits. Non-idealities in the power supply, such as voltage fluctuations or noise, can directly affect the output current or voltage, causing inaccuracies or instability.
How to apply SJAl000?
The register and pin configuration of SJAl000 allows it to use a wide variety of integrated or discrete CAN transceivers.Since there are different microcontrollers connected to 1:3, different microcontrollers can be used in the application.Figure 10.6 shows a typical SJAl000 application that includes an 80C51 microcontroller and a PCA82C251 transceiver.It can also be controlled by an address decoder, such as when the address/data bus is used for other peripheral devices.
How to solve the problem of poor service quality at the network layer?
Poor service quality at the network layer can be caused by various factors, such as network congestion, latency, packet loss, or inadequate network infrastructure. Here are some steps you can take to help solve the problem:
- Identify the Issue: Begin by identifying and understanding the specific aspects of service quality that are causing problems. This could involve analyzing network performance metrics, monitoring network traffic, and collecting data on the observed issues. Identify the symptoms, patterns, and potential causes of the poor service quality.
- Analyze Network Infrastructure: Evaluate the network infrastructure, including routers, switches, cables, and other network components. Ensure that the network equipment is functioning correctly, configured properly, and capable of handling the expected traffic load. Check for any bottlenecks, outdated hardware, or faulty components that may be contributing to the poor service quality.
- Optimize Network Configuration: Review the network configuration settings to ensure they are optimized for performance. This includes proper routing, Quality of Service (QoS) settings, traffic prioritization, and network addressing. Adjust the configuration based on the specific requirements of the network and the applications being used to improve service quality.
- Manage Network Congestion: Network congestion is a common cause of poor service quality. Implement traffic management techniques such as traffic shaping, packet prioritization, and congestion control algorithms. These techniques can help regulate the flow of traffic, prevent network congestion, and ensure fair distribution of network resources.
- Enhance Bandwidth: Insufficient bandwidth can lead to degraded service quality. Evaluate the network bandwidth requirements and consider upgrading the network infrastructure to meet the demands. This may involve increasing the capacity of network links, upgrading to higher-speed connections, or implementing link aggregation techniques.
- Monitor and Troubleshoot: Implement network monitoring tools to continuously monitor network performance and identify any issues in real-time. Proactively troubleshoot and address any anomalies or performance degradation as soon as they are detected. This can help in quickly identifying the root causes of poor service quality and taking appropriate corrective actions.
- Consider Network Redundancy: Implementing network redundancy can improve service quality by providing alternative paths in case of network failures. Redundant links, routers, or service providers can help maintain network availability and reduce the impact of outages on service quality.
- Work with Service Providers: If poor service quality is related to the connectivity provided by an Internet Service Provider (ISP), establish communication with the ISP’s technical support team. Report the issue, provide detailed information about the problem, and work together to diagnose and resolve the underlying causes.
- Continuous Improvement: Network performance and service quality are ongoing concerns. Regularly review and assess the network infrastructure, monitor performance metrics, and gather user feedback to identify areas for improvement. Stay updated with industry best practices, emerging technologies, and advancements in networking to continually optimize service quality.
What are the 32-bit registers accessible to the internal user of the ARM processor?
The ARM processor architecture includes several 32-bit registers that are accessible to the internal user. These registers can be broadly categorized into the following types:
General-Purpose Registers (GPRs):
- R0-R12: These are the general-purpose registers used for general computation and storage of intermediate values during program execution.
- R13 (SP): Stack Pointer register, used to point to the current location in the stack.
- R14 (LR): Link Register, used to store the return address when executing subroutine calls.
- R15 (PC): Program Counter, holds the memory address of the next instruction to be fetched and executed.
Status Registers:
- CPSR (Current Program Status Register): Contains various status flags and control bits, such as the condition code flags (N, Z, C, V), interrupt enable/disable bit (I), and processor mode bits.
Saved Program Status Registers (SPSRs):
- SPSR_fiq: Saved Program Status Register for FIQ mode.
- SPSR_svc: Saved Program Status Register for Supervisor mode.
- SPSR_abt: Saved Program Status Register for Abort mode.
- SPSR_und: Saved Program Status Register for Undefined mode.
- SPSR_irq: Saved Program Status Register for IRQ mode.
Banked Registers:
- R8_fiq-R12_fiq: These registers are banked in FIQ mode and are used exclusively in that mode.
- R13_svc-R14_svc: These registers are banked in Supervisor mode.
- R13_abt-R14_abt: These registers are banked in Abort mode.
- R13_und-R14_und: These registers are banked in Undefined mode.
- R13_irq-R14_irq: These registers are banked in IRQ mode.
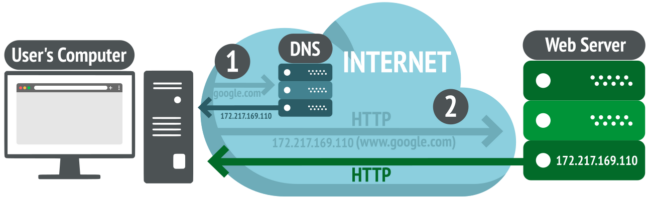
What is the principle of Web Server implementation?
The principle of Web Server implementation involves several key elements and concepts:
- Client-Server Model: Web servers operate on a client-server architecture, where clients (typically web browsers) send HTTP requests to the server, and the server responds with the requested content. The server listens for incoming requests and handles them accordingly.
- Networking: Web servers use network protocols to communicate with clients. The Hypertext Transfer Protocol (HTTP) is the primary protocol for web communication. Web servers listen on a specific port (usually port 80 for HTTP) for incoming requests from clients.
- IP Address and Domain Name: A web server is associated with an IP address, which serves as its unique identifier on the internet. Clients can access the server using the server’s IP address or a domain name, which maps to the IP address through DNS (Domain Name System).
- Request Handling: When a client sends an HTTP request to a web server, the server receives and processes the request. It extracts information from the request, such as the requested resource (identified by the URL), HTTP method (e.g., GET, POST), headers, and query parameters.
- Content Generation: Based on the requested resource, the web server generates the appropriate content to fulfill the request. This can involve fetching static files (e.g., HTML, CSS, images) from the server’s file system or dynamically generating content by executing server-side scripts (e.g., PHP, Python, Node.js) or interacting with databases.
- Response Generation: Once the content is generated, the web server constructs an HTTP response. It sets the appropriate response status code (e.g., 200 for successful, 404 for not found) and includes response headers (e.g., content type, caching directives) to provide additional information about the response.
- Content Delivery: The web server sends the HTTP response back to the client over the network. The response is typically broken down into packets and transmitted using the TCP/IP protocol suite. The client receives and reassembles the packets to reconstruct the complete response.
- Security: Web servers implement various security measures to protect the server and client data. This includes implementing encryption using SSL/TLS (HTTPS), enforcing access control mechanisms, employing firewalls, and mitigating common web vulnerabilities (e.g., cross-site scripting, SQL injection).
- Scalability and Performance: Web servers are designed to handle multiple concurrent requests efficiently. Techniques like multi-threading, asynchronous processing, connection pooling, caching, load balancing, and content delivery networks (CDNs) are employed to ensure high performance and scalability.
- Logging and Monitoring: Web servers often maintain logs of incoming requests, capturing details such as client IP addresses, requested URLs, response times, and errors. Monitoring tools can analyze these logs to gain insights into server performance, identify issues, and track usage patterns.
According to whether the IC card and the IC card reader need to be in contact to read and write data, what can the IC card be divided into?
Based on the requirement for contact between the IC card and the IC card reader to read and write data, IC cards can be divided into two main types:
- Contact IC Cards: Contact IC cards require physical contact between the card and the card reader for data transfer. These cards have metallic contacts or pads embedded on the surface, which establish electrical connections with the card reader when inserted into the reader’s slot. The contacts facilitate communication and power transfer between the card and the reader. Examples of contact IC cards include traditional smart cards, such as credit cards with embedded chips and SIM cards used in mobile phones.
- Contactless IC Cards: Contactless IC cards, also known as proximity cards or RFID (Radio Frequency Identification) cards, do not require physical contact with the card reader. Instead, they utilize wireless communication using radio frequency (RF) technology. The card reader emits an RF field, and the contactless card has an embedded antenna that receives the reader’s signal and transmits data wirelessly. This allows for convenient and faster interaction between the card and the reader. Examples of contactless IC cards include access cards, transportation cards (e.g., contactless payment cards), and electronic toll collection cards.
What are the characteristics of dual in-line Integrated Circuits(ICs)s?
Dual in-line Integrated Circuits (ICs) are electronic components that have specific characteristics and configurations. Here are the key characteristics of dual in-line ICs:
- Package Type: Dual in-line ICs are packaged in a dual in-line package (DIP). This package consists of a rectangular-shaped body with two parallel rows of pins or leads extending from opposite sides. The pins are arranged in a dual in-line configuration, hence the name.
- Pin Count: Dual in-line ICs typically have a higher pin count compared to other package types. Common pin counts for DIP packages range from 8 to 64 pins, although higher pin count versions are also available.
- Through-Hole Mounting: Dual in-line ICs use through-hole mounting, which means the leads are inserted into holes on a printed circuit board (PCB) and soldered on the opposite side of the board. This mounting method provides stability and reliability.
- General Purpose: Dual in-line ICs are commonly used for general-purpose applications and can be found in various electronic devices and systems. They are available in a wide range of IC types, including logic gates, microcontrollers, memory chips, amplifiers, and many other integrated circuits.
- Ease of Replacement: Dual in-line ICs are relatively easy to replace or remove from a PCB. Their through-hole mounting allows for straightforward removal and replacement using standard soldering techniques. This characteristic makes them suitable for repair and maintenance purposes.
- Breadboard Compatibility: Dual in-line ICs are compatible with solderless breadboards, which are prototyping platforms used to build and test electronic circuits. The DIP package can be easily plugged into the breadboard’s socket to create and experiment with various circuit configurations.
- Legacy Technology: Dual in-line ICs have been widely used since the early days of integrated circuits. However, with advancements in technology and miniaturization, other package types such as surface-mount technology (SMT) have gained popularity. Consequently, dual in-line ICs are less commonly used in modern, high-density electronic designs.
What is a network manager?
Dual in-line Integrated Circuits (ICs) are electronic components that have specific characteristics and configurations. Here are the key characteristics of dual in-line ICs:
- Package Type: Dual in-line ICs are packaged in a dual in-line package (DIP). This package consists of a rectangular-shaped body with two parallel rows of pins or leads extending from opposite sides. The pins are arranged in a dual in-line configuration, hence the name.
- Pin Count: Dual in-line ICs typically have a higher pin count compared to other package types. Common pin counts for DIP packages range from 8 to 64 pins, although higher pin count versions are also available.
- Through-Hole Mounting: Dual in-line ICs use through-hole mounting, which means the leads are inserted into holes on a printed circuit board (PCB) and soldered on the opposite side of the board. This mounting method provides stability and reliability.
- General Purpose: Dual in-line ICs are commonly used for general-purpose applications and can be found in various electronic devices and systems. They are available in a wide range of IC types, including logic gates, microcontrollers, memory chips, amplifiers, and many other integrated circuits.
- Ease of Replacement: Dual in-line ICs are relatively easy to replace or remove from a PCB. Their through-hole mounting allows for straightforward removal and replacement using standard soldering techniques. This characteristic makes them suitable for repair and maintenance purposes.
- Breadboard Compatibility: Dual in-line ICs are compatible with solderless breadboards, which are prototyping platforms used to build and test electronic circuits. The DIP package can be easily plugged into the breadboard’s socket to create and experiment with various circuit configurations.
- Legacy Technology: Dual in-line ICs have been widely used since the early days of integrated circuits. However, with advancements in technology and miniaturization, other package types such as surface-mount technology (SMT) have gained popularity. Consequently, dual in-line ICs are less commonly used in modern, high-density electronic designs.
What are the working electrodes and auxiliary electrodes, respectively?
In electrochemical systems, such as electrochemical cells or sensors, working electrodes and auxiliary electrodes are two types of electrodes that serve different purposes:
- Working Electrodes: Working electrodes are the primary electrodes involved in the electrochemical reaction of interest. They are designed to facilitate the transfer of electrons between the analyte (the substance being analyzed) and the electrode surface. The working electrode is where the chemical reaction takes place, and its properties and surface characteristics can influence the rate and nature of the electrochemical process. The working electrode is typically made of a conductive material, such as platinum, gold, glassy carbon, or other materials depending on the specific application.
- Auxiliary Electrodes: Auxiliary electrodes, also known as counter electrodes or reference electrodes, are additional electrodes used to complete the electrical circuit in an electrochemical cell. They provide a pathway for the current to flow, compensating for the changes in charge that occur at the working electrode. The role of the auxiliary electrode is to maintain a constant potential or current and ensure the balance of charges during the electrochemical process. Common materials used for auxiliary electrodes include platinum, graphite, or other stable and conductive materials.
What is the main source of BJT (bipolar triode) noise?
The main source of noise in a Bipolar Junction Transistor (BJT) is thermal noise, also known as Johnson-Nyquist noise. Thermal noise arises due to the random thermal motion of electrons and holes within the BJT.
The thermal noise in a BJT is primarily caused by two factors:
- Base Current Fluctuations: The base region of a BJT has a thin layer of material, which results in a relatively high resistance. The thermal noise associated with this resistance leads to random fluctuations in the base current. These fluctuations can get amplified by the transistor’s current gain, resulting in noise at the output.
- Collector Current Fluctuations: The collector current of a BJT is determined by the base current and the transistor’s current gain. The random fluctuations in the base current due to thermal noise will consequently lead to fluctuations in the collector current.


COMMENTS